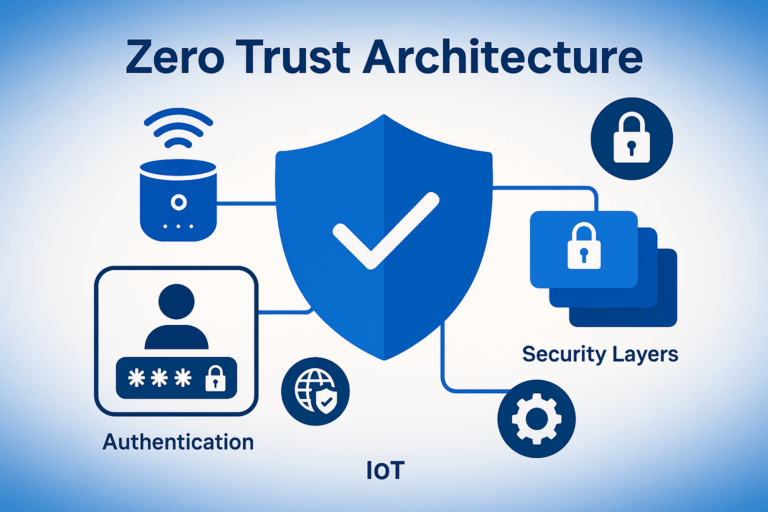
Securing IoT Devices with Zero Trust Architecture
A Complete Guide for 2025 🔐 Introduction: The IoT Security Challenge in the Zero…

A Complete Guide for 2025 🔐 Introduction: The IoT Security Challenge in the Zero…

Email is increasingly becoming an essential tool for communication in the contemporary digital world.…

The clock is ticking for organizations around the globe as the Payment Card Industry…

An overview of penetration testing and bug bounty programs by Devolity. In the ever-evolving…

The consequences of a data breach involving payment card information can be devastating and…

[CIVN-2024-0031] Multiple Vulnerabilities in Google Chrome OS Indian – Computer Emergency Response Team (cert-in.org.in)…

Denial of Service Vulnerability in Cisco Indian – Computer Emergency Response Team (cert-in.org.in) Severity…

Ubuntu Server is a popular open-source operating system used in a wide range of…

By- Indian – Computer Emergency Response Team (cert-in.org.in) Severity Rating: Critical Overview Multiple hacktivist…