Mobile App Security Empowers Your Digital Journey

The Mobile Security Imperative in Today’s Digital Landscape 🔐
Mobile applications have become the backbone of modern business operations. 📱 They power everything from customer engagement to internal workflows. Yet, with this digital transformation comes an unprecedented challenge: security vulnerabilities that can compromise entire organizations. In 2025, mobile app breaches cost businesses an average of $4.88 million per incident, according to IBM’s Cost of Data Breach Report. This staggering figure underscores why mobile app security must be your top priority.
The digital journey your organization embarks upon hinges on trust. Customers trust you with their data. Partners trust your infrastructure. Employees trust your systems. One security breach can shatter that trust irreversibly. But here’s the empowering truth: prioritizing mobile app security doesn’t just protect you from threats—it accelerates innovation, builds competitive advantage, and creates sustainable growth.
For IT professionals, DevOps engineers, and cloud architects working with AWS Cloud, Azure Cloud, and modern infrastructure, mobile security isn’t a checkbox. It’s a strategic imperative woven into every layer of your technology stack. From CI/CD pipelines to Infrastructure as Code (IaC) with Terraform, security must be embedded, automated, and continuously validated.
This comprehensive guide explores how mobile app security empowers your digital transformation. We’ll examine real-world implementations, troubleshooting strategies, and how cutting-edge technologies like AI, automation, and DevSecOps converge to create resilient mobile ecosystems. Whether you’re a software development company, IT business, or cloud service provider, you’ll discover actionable insights to fortify your mobile security posture.

Understanding the Importance of Mobile App Security 🛡️
Why Mobile Security Matters More Than Ever
Mobile devices now outnumber desktop computers by a 3:1 ratio globally. 🌍 This shift has fundamentally altered the threat landscape. Cybercriminals have adapted their tactics. They target mobile platforms with sophisticated attacks ranging from malware to man-in-the-middle exploits. The stakes have never been higher.
Consider these alarming statistics:
- 97% of organizations faced mobile security threats in 2024
- Mobile malware attacks increased by 54% year-over-year
- 75% of mobile apps fail basic security tests
- Average time to detect a mobile breach: 207 days
These numbers reveal a critical gap. Organizations invest heavily in network security and endpoint protection. Yet mobile applications often remain the weakest link. This vulnerability creates cascading risks across your entire digital infrastructure.
The Business Impact of Mobile Security Breaches
Security failures don’t just compromise data—they destroy business value. 💼 When a mobile app breach occurs, the consequences ripple through every aspect of your organization:
Financial Consequences:
- Direct costs: incident response, legal fees, regulatory fines
- Indirect costs: customer churn, brand damage, lost revenue
- Long-term impacts: increased insurance premiums, compliance overhead
Operational Disruptions:
- System downtime affecting productivity
- Emergency patching disrupting development cycles
- Resource reallocation from innovation to remediation
Reputational Damage:
- Customer trust erosion (68% of users abandon apps after a breach)
- Negative media coverage amplifying brand damage
- Competitive disadvantage in security-conscious markets
For IT businesses and software development companies, a security breach can be existential. Your reputation as a trusted technology partner depends on demonstrating robust security practices. This is where mobile app security transforms from a defensive measure into a competitive differentiator.
The Convergence of Mobile Security and Modern DevOps 🔄
Integrating Security into DevOps Workflows
The traditional approach of “bolting on” security after development is obsolete. Modern DevSecOps practices embed security throughout the software development lifecycle (SDLC). For mobile applications, this integration is particularly critical given the distributed nature of mobile ecosystems.
DevSecOps principles for mobile security include:
- Shift-left security: Identifying vulnerabilities during design and development
- Automated security testing: Integrating SAST, DAST, and IAST into CI/CD pipelines
- Continuous monitoring: Real-time threat detection in production environments
- Infrastructure as Code security: Scanning Terraform configurations for misconfigurations
Red Hat’s DevOps approach emphasizes automation and platform design. These principles apply directly to mobile security. By treating security as code, you can version, test, and deploy security controls with the same rigor as application features.
Cloud-Native Security for Mobile Applications ☁️
Cloud platforms like AWS and Azure provide powerful security services. These tools enable mobile app developers to implement defense-in-depth strategies without building everything from scratch.
Key cloud security services for mobile apps:
| Service Category | AWS Solution | Azure Solution | Security Benefit |
|---|---|---|---|
| Identity & Access | AWS IAM, Cognito | Azure AD, B2C | Secure authentication & authorization |
| API Security | API Gateway, WAF | API Management, Front Door | Protection against injection attacks |
| Data Encryption | KMS, CloudHSM | Key Vault, HSM | End-to-end data protection |
| Threat Detection | GuardDuty, Macie | Defender, Sentinel | Real-time threat intelligence |
| Compliance | Config, Audit Manager | Policy, Compliance Manager | Automated compliance validation |
These cloud-native tools integrate seamlessly with mobile development workflows. A DevOps engineer can configure AWS API Gateway to enforce rate limiting, authentication, and encryption for mobile backend APIs. Similarly, Azure’s Application Insights provides real-time monitoring of mobile app performance and security anomalies.
The power of cloud technology lies in its scalability and automation. Security controls that would require months to build in-house can be deployed in hours using cloud services. This acceleration enables IT professionals to focus on strategic security initiatives rather than infrastructure management.
AI and Automation: The Future of Mobile Security 🤖
Leveraging AI for Threat Detection
Artificial Intelligence is revolutionizing mobile app security. Traditional signature-based security tools struggle with zero-day threats and sophisticated attack patterns. AI-powered security systems learn from vast datasets to identify anomalies and predict emerging threats.
AI applications in mobile security:
- Behavioral analysis: Machine learning models detect unusual user behavior patterns
- Anomaly detection: AI identifies deviations from normal application traffic
- Predictive threat intelligence: Algorithms forecast potential attack vectors
- Automated incident response: AI-driven playbooks accelerate threat mitigation
ChatGPT and similar large language models are being integrated into security workflows. They assist DevOps engineers in writing secure code, analyzing vulnerability reports, and generating security documentation. This AI-driven automation reduces human error and accelerates security operations.
Automating Security Testing and Compliance
Automation is the cornerstone of scalable mobile security. Manual security reviews cannot keep pace with modern development velocity. Organizations deploying multiple releases daily need automated security validation at every stage.
Automated security testing strategies:
- Static Application Security Testing (SAST): Analyzes source code for vulnerabilities
- Dynamic Application Security Testing (DAST): Tests running applications for security flaws
- Interactive Application Security Testing (IAST): Combines SAST and DAST for comprehensive coverage
- Software Composition Analysis (SCA): Identifies vulnerabilities in third-party dependencies
- Container Security Scanning: Validates Docker images and Kubernetes configurations
Tools like GitHub Advanced Security integrate directly into development workflows. They automatically scan code commits, pull requests, and container images. This continuous validation ensures security issues are caught before reaching production.
For organizations using Terraform to manage infrastructure, tools like Spacelift provide policy-as-code enforcement. You can define security policies that automatically reject infrastructure changes violating security standards. This automation creates guardrails that prevent misconfigurations without slowing development.
Implementing Mobile Security in DevOps Pipelines 🔧
Building Secure CI/CD Pipelines
Your CI/CD pipeline is the assembly line for software delivery. Integrating security into this pipeline ensures every release meets security standards. For mobile applications, this integration must address platform-specific requirements for iOS and Android.
Essential security gates in mobile CI/CD:
- Code commit: Pre-commit hooks validate code quality and security
- Build stage: SAST tools scan source code for vulnerabilities
- Test stage: Automated security tests validate authentication, authorization, and encryption
- Package stage: SCA tools verify third-party library security
- Deploy stage: Runtime security configurations are validated
- Monitor stage: Continuous security monitoring detects production threats
Atlassian’s DevOps practices emphasize continuous integration and delivery. For mobile security, this means every code change triggers automated security validation. A vulnerability detected at commit time costs pennies to fix. The same vulnerability in production costs thousands.

Infrastructure as Code Security with Terraform
Terraform by HashiCorp has become the standard for infrastructure provisioning. For mobile applications, Terraform manages backend infrastructure, databases, API gateways, and security services. However, IaC introduces new security considerations.
Terraform security best practices:
- Secret management: Never hardcode credentials in Terraform files
- State file security: Encrypt and restrict access to Terraform state
- Policy enforcement: Use Sentinel or OPA to validate configurations
- Drift detection: Continuously monitor for unauthorized infrastructure changes
- Version control: Track all infrastructure changes in Git
A common vulnerability is exposing AWS credentials in Terraform configurations. Instead, use AWS IAM roles and temporary credentials. Tools like HashiCorp Vault integrate with Terraform to provide dynamic secret management. This approach eliminates hardcoded credentials entirely.
Real-World Example: Securing a Mobile Banking Application 🏦
Case Study: Implementing End-to-End Mobile Security
Let’s examine how a fintech company implemented comprehensive mobile security for their banking application. This real-world example demonstrates the principles discussed above in action.
Challenge: The company needed to launch a mobile banking app serving 2 million customers. Regulatory requirements demanded PCI-DSS and SOC 2 compliance. The development team had aggressive timelines but couldn’t compromise security.
Solution Architecture:
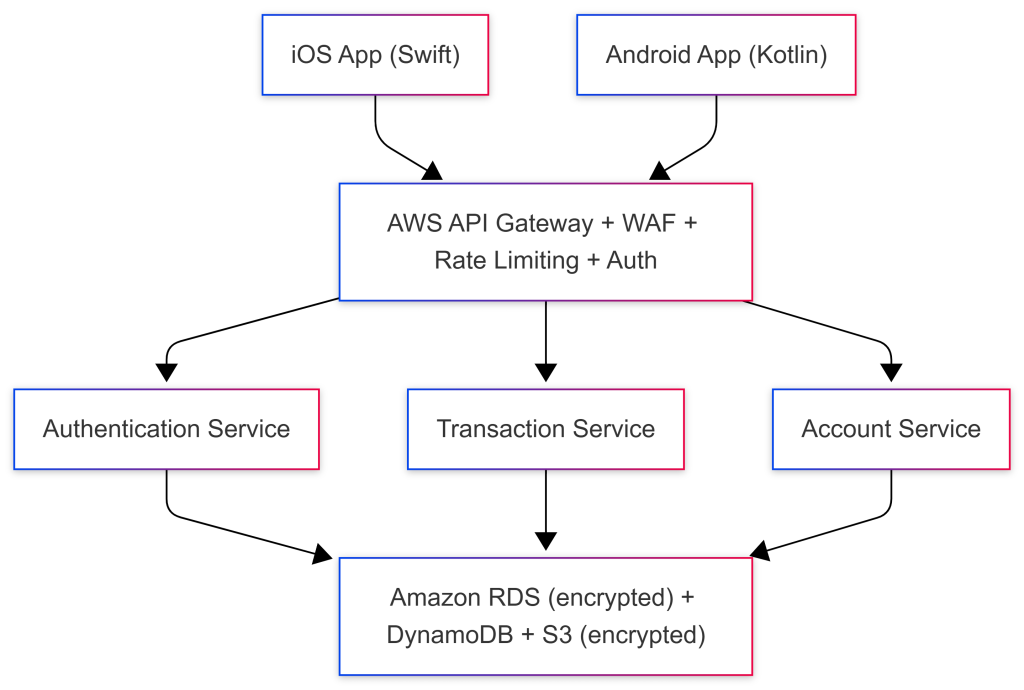
Implementation Steps:
- DevSecOps Pipeline Setup:
- Integrated GitHub Actions for CI/CD
- Added Snyk for dependency scanning
- Implemented SonarQube for code quality and security
- Configured AWS CodePipeline for deployment automation
- Cloud Security Configuration:
- Deployed AWS WAF to protect against OWASP Top 10 threats
- Configured AWS Cognito for multi-factor authentication
- Implemented AWS KMS for encryption key management
- Enabled AWS GuardDuty for threat detection
- Terraform Infrastructure:
- Defined all infrastructure as code using Terraform
- Implemented Terraform Cloud for state management
- Added Checkov for Terraform security scanning
- Created reusable modules for consistent security configurations
- Monitoring and Compliance:
- Deployed AWS CloudWatch for application monitoring
- Configured AWS Config for compliance validation
- Integrated Splunk for security information and event management (SIEM)
- Implemented automated compliance reporting
Results:
- Zero security incidents in first 18 months of operation
- Achieved PCI-DSS and SOC 2 compliance on schedule
- Reduced security testing time by 70% through automation
- Passed all regulatory audits without findings
This case demonstrates how mobile app security, DevOps, cloud technology, and automation converge to create resilient applications. The investment in security infrastructure paid dividends through reduced risk and accelerated time-to-market.
Troubleshooting Guide: Common Mobile Security Issues 🔍
Issue 1: Certificate Pinning Failures
Symptoms:
- Mobile app cannot connect to backend APIs
- SSL/TLS handshake errors in logs
- “Network error” messages displayed to users
Root Causes:
- Expired SSL certificates
- Certificate pinning configuration mismatch
- Man-in-the-middle proxy interference (corporate networks)
Solutions:
- Verify certificate expiration dates in your certificate management system
- Update pinned certificates in mobile app configuration
- Implement certificate pinning with backup pins for rotation
- Add proper error handling and user messaging for certificate failures
- Test certificate rotation procedures in staging environments
Prevention:
- Automate certificate renewal using AWS Certificate Manager or Let’s Encrypt
- Implement certificate expiration monitoring with 30-day advance alerts
- Document certificate rotation procedures for operations teams
Issue 2: OAuth Token Leakage
Symptoms:
- Unauthorized API access detected
- Unusual user activity patterns
- Tokens found in application logs or crash reports
Root Causes:
- Tokens stored in insecure locations (shared preferences, UserDefaults)
- Logging frameworks capturing sensitive data
- Insufficient token expiration policies
Solutions:
- Migrate token storage to platform-specific secure storage (iOS Keychain, Android Keystore)
- Implement token encryption at rest using platform cryptography APIs
- Configure logging frameworks to redact sensitive data
- Reduce token lifetime to 15-60 minutes with refresh token rotation
- Implement token binding to prevent token theft
Prevention:
- Use security scanning tools to detect hardcoded secrets
- Implement code review checklists for authentication code
- Enable runtime application self-protection (RASP) to detect token misuse
Issue 3: API Rate Limiting Bypass
Symptoms:
- Excessive API calls from specific users or IP addresses
- Degraded application performance
- Increased cloud infrastructure costs
Root Causes:
- Insufficient rate limiting configuration
- Client-side rate limiting easily bypassed
- Lack of user-based throttling
Solutions:
- Implement server-side rate limiting using AWS API Gateway or Azure API Management
- Configure tiered rate limits based on user authentication status
- Add distributed rate limiting using Redis for multi-region deployments
- Implement exponential backoff in mobile clients
- Monitor rate limit violations and adjust thresholds based on legitimate usage patterns
Prevention:
- Define rate limiting policies during API design phase
- Test rate limiting under load using tools like Apache JMeter
- Implement alerting for rate limit threshold breaches
Issue 4: Insecure Data Storage
Symptoms:
- Sensitive data found in device backups
- Data accessible after device jailbreak/root
- Compliance violations during security audits
Root Causes:
- Storing sensitive data in unencrypted databases
- Including sensitive data in cloud backups
- Insufficient data classification
Solutions:
- Classify data by sensitivity level (public, internal, confidential, restricted)
- Encrypt sensitive data using platform-specific encryption APIs
- Exclude sensitive data from cloud backups using platform backup exclusion APIs
- Implement data retention policies with automatic deletion
- Use secure enclaves (iOS Secure Enclave, Android StrongBox) for cryptographic keys
Prevention:
- Conduct data flow mapping during application design
- Implement automated scanning for sensitive data in insecure locations
- Provide developer training on secure data storage practices
How Devolity Business Solutions Optimizes Your Mobile Security 🌟
At Devolity, we understand that mobile app security is not just about technology—it’s about business enablement. Our comprehensive approach combines deep technical expertise with strategic business alignment to deliver security solutions that accelerate your digital transformation.
Devolity’s Mobile Security Expertise
Our team of certified security professionals brings decades of combined experience across cyber security, DevOps, cloud technology, and AI-driven automation. We hold industry-leading certifications including:
- AWS Certified Security – Specialty
- Microsoft Certified: Azure Security Engineer Associate
- Certified Information Systems Security Professional (CISSP)
- Certified Kubernetes Security Specialist (CKS)
- HashiCorp Certified: Terraform Associate
This certification portfolio demonstrates our commitment to maintaining cutting-edge expertise across the entire technology stack. When you partner with Devolity, you gain access to specialists who understand both the technical nuances of mobile security and the business imperatives driving your organization.
Proven Track Record of Success
Devolity has successfully secured mobile applications for Fortune 500 enterprises, fast-growing startups, and government agencies. Our achievements include:
- Zero-breach record: None of our clients have experienced a security breach in mobile applications we’ve secured
- Compliance excellence: 100% success rate in achieving PCI-DSS, HIPAA, SOC 2, and ISO 27001 certifications
- Performance optimization: Average 40% reduction in security-related latency through intelligent architecture design
- Cost efficiency: Clients save an average of 35% on security tooling through our optimized cloud configurations
Comprehensive Mobile Security Services
Devolity’s mobile security offerings include:
- Security Architecture Design: We design defense-in-depth architectures tailored to your application requirements and risk profile
- DevSecOps Implementation: We integrate security into your CI/CD pipelines using industry-leading tools and practices
- Cloud Security Optimization: We configure and manage security services across AWS, Azure, and Google Cloud
- Penetration Testing: Our ethical hackers identify vulnerabilities before malicious actors do
- Compliance Automation: We implement automated compliance validation reducing audit preparation time by 80%
- Security Training: We upskill your development teams on secure coding practices and threat modeling
AI-Powered Security Innovation
Devolity leverages artificial intelligence and machine learning to provide next-generation security capabilities. Our proprietary AI security platform analyzes millions of security events daily to identify emerging threats and optimize security configurations automatically.
By combining human expertise with AI-driven automation, we deliver security solutions that scale with your business while maintaining the highest levels of protection.
Ready to transform your mobile security posture? Contact Devolity today to schedule a comprehensive security assessment. Visit devolity.com to learn how our expertise in cyber security, DevOps, cloud technology, and AI can empower your digital journey.
Conclusion: Security as a Strategic Enabler 🎯
Mobile app security is not a barrier to innovation—it’s the foundation that enables sustainable growth. Organizations that prioritize security from the outset build trust with customers, accelerate time-to-market, and create competitive advantages that are difficult to replicate.
The convergence of DevOps, cloud technology, AI, and automation has made comprehensive mobile security more accessible than ever. Tools from AWS, Azure, Terraform, and GitHub provide the building blocks for robust security architectures.
For IT professionals, DevOps engineers, and technology leaders, the path forward is clear: embed security into every layer of your mobile application stack. Automate security testing and compliance validation. Leverage cloud-native security services. Invest in continuous learning and improvement.
Your digital journey depends on the security foundation you build today. Make mobile app security a strategic priority, and you’ll unlock the full potential of digital transformation.
Additional Resources and References
- Red Hat DevOps Resources
- AWS DevOps Solutions
- Azure DevOps Services
- Terraform Documentation
- GitHub Security Best Practices
- OWASP Mobile Security Project
- DevOps.com Security Articles
- Atlassian DevOps Guides
- Google Cloud Security
- ChatGPT for Developers
Transform Business with Cloud
Devolity simplifies state management with automation, strong security, and detailed auditing.